
Aim:
Implement the data link layer framing methods such as Bit Stuffing.
- Program To Implement Crc In Java
- Program To Implement Crc In Java Developer
- Program To Implement Crc In Java Runtime
- Program To Implement Crc In Java Compiler
- Program To Implement Crc In Javascript
Theory
- Next Project: Java program to reverse a string and to check palindrome or not: Previous Project: Constructor and destructor: Return to Project Index: Post New Project: Related Projects. C program for Multiple Stack; C program to perform various operation on STACK; C program to implement a STACK; C program to perform operation on Double Link List.
- I am having problems with calculating CRC-16 implementation of a byte array in java. Basically I am trying to send bytes to a RFID that starts writing to a tag. I can see the checksum value of array by looking tcpdump command on mac. But my goal is to generate it by myself. Here is my byte array which should generate 0xbe,0xd9.
Security and Error detection are the most prominent features that are to be provided by any application which transfers data from one end to the other end. One of such a mechanism in tracking errors which may add up to the original data during transfer is known as Stuffing. It is of two types namely Bit Stuffing and the other Character Stuffing. Coming to the Bit Stuffing, 01111110 is appended within the original data while transfer of it. The following program describes how it is stuffed at the sender end and de-stuffed at the reciever end.
Which CRC-32 algorithm is used in the Java CRC-32 class? The java doc does not give any details. What is the polynomail used and the initial value for calculaton?
ArrayList is the most popular implementation of List in java. ArrayList is very similar to Array but provides the feature of dynamic space allocation when the number of objects in the list grows. In Array, we have to provide the size at the time of initialization but that is not required for ArrayList. Simple Program to generate CRC and check error.
Program:
#include
main()
{
int a[15];
int i,j,k,n,c=0,pos=0;
clrscr();
printf('n Enter the number of bits');
scanf('%d',&n);
printf('n Enter the bits');
for(i=0;i<>
scanf('%d',&a[i]);
for(i=0;i<>
{
if(a[i]1)
{
c++;
if(c5)
{
pos=i+1;
c=0;
for(j=n;j>=pos;j--)
{
k=j+1;
a[k]=a[j];
}
a[pos]=0;
n=n+1;
}
}
else
c=0;
}
printf('n DATA AFTER STUFFING n');
printf(' 01111110 ');
for(i=0;i<>
{
printf('%d',a[i]);
}
printf(' 01111110 ');
getch();
}
Output:
Aim:
Implement the data link layer framing methods such as Character Stuffing and also De-stuff it
Theory
Coming to the Character Stuffing, DLESTX and DLEETX are used to denote start and end of character data with some constraints imposed on repetition of charaters as shown in the program below clearly.
Program:
#include
#include
#include
void charc(void);
void main()
{
int choice;
while(1)
{
printf('nnn1.character stuffing');
printf('nn2.exit');
printf('nnnenter choice');
scanf('%d',&choice);
printf('%d',choice);
if(choice>2)
printf('nn invalid option..please renter');
switch(choice)
{
case 1:
charc();
break;
case 2:
exit(0);
}
}
}
void charc(void)
{
char c[50],d[50],t[50];
int i,m,j;
clrscr();
printf('enter the number of charactersn');
scanf('%d',&m);
printf('n enter the charactersn');
for(i=0;i<>
{
scanf('%c',&c[i]);
}
printf('n original datan');
for(i=0;i<>
printf('%c',c[i]);
d[0]='d';
d[1]='l';
d[2]='e';
d[3]='s';
d[4]='t';
d[5]='x';
for(i=0,j=6;i<>
{
if((c[i]'d'&&c[i+1]'l'&& c[i+2]'e'))
{
d[j]='d';
j++;
d[j]='l';
j++;
d[j]='e';
j++;
m=m+3;
}
d[j]=c[i];
}
m=m+6;
m++;
d[m]='d';
m++;
d[m]='l';
m++;
d[m]='e';
m++;
d[m]='e';
m++;
d[m]='t';
m++;
d[m]='x';
m++;
printf('nn transmitted data: n');
for(i=0;i<>
{
printf('%c',d[i]);
}
for(i=6,j=0;i<>
{
if(d[i]'d'&&d[i+1]'l'&&d[i+2]'e'&&d[i+3]'d'&&d[i+4]'l'&&d[i+5]'e')
i=i+3;
t[j]=d[i];
}
printf('nnreceived data:');
for(i=0;i<>
{printf('%c',t[i]);
}
}
Output:
Aim:
Implement on a data set of characters the CRC polynomials.
Theory
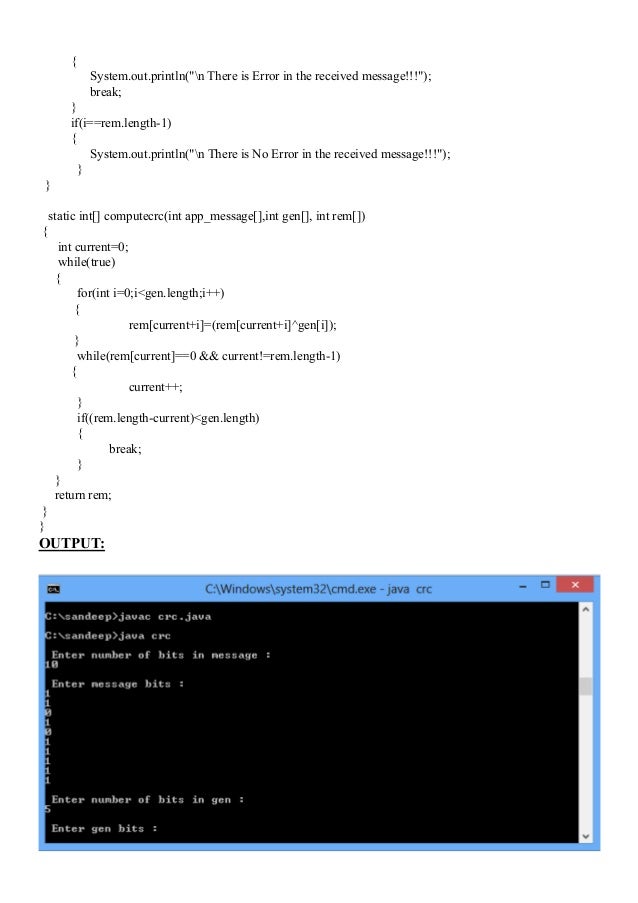
CRC means Cyclic Redundancy Check. It is the most famous and traditionally successful mechanism used in error detection through the parity bits installed within the data and obtaining checksum which acts as the verifier to check whether the data retreived at the reciever end is genuine or not. Various operations are involved in implementing CRC on a data set through CRC generating polynomials. In the program, I have also provided the user to opt for Error detection whereby he can proceed for it. Understand the program below as it is much simpler than pretented to be so.
Program:
#include
#include
#include
#define N strlen(g)
char t[128], cs[128], g[]='100010000';
int a, e, c;
void xor() {
for(c=1;c
void crc() {
for(e=0;e
if(cs[0]'1') xor();
for(c=0;c
}while(e<=a+N-1);
}
void main() {
clrscr();
printf('nEnter poly : '); scanf('%s',t);
printf('nGenerating Polynomial is : %s',g);
a=strlen(t);
for(e=a;e printf('nModified t[u] is : %s',t);
crc();
printf('nChecksum is : %s',cs);
for(e=a;e printf('nFinal Codeword is : %s',t);
printf('nTest Error detection 0(yes) 1(no) ? : ');
scanf('%d',&e);
if(e0) {
printf('Enter position where error is to inserted : ');
scanf('%d',&e);
t[e]=(t[e]'0')?'1':'0';
printf('Errorneous data : %sn',t);
}
crc();
for (e=0;(e<>
if(e
getch();
}
Output:
Aim:
Implement Dijkstra's algorithm to compute the Shortest path through a graph.
Theory
Dijkstra's algorithm is a non-adaptive routing algorithm which is very widely used to route packets from source to detination through various routers available during the transmission. It is implemented at the network layer of the architecture where data packets are sent through routers which maitain routing tables that help to denote the exact location to where the destined packets need to be delivered. Major advantage in using Dijkstra's algorithm is that it forwards the data packets from source to destination through the most optimized path in terms of both the distance and cost observed. It prompts the user to enter the number of nodes and the source and destination nodes among them. In addition, the algorithm written below also asks for the neighbours to each node with the distances to reach to them from each node is also prompted. All this data is stored and used further to calculate and estimate the best path possible for data packets to reach their destination from source. Program below explains it in a much better way.
Program:
#include
#include
int n,s,nb,nbs[15],snbs[15],delay[15][15],i,j,temp[15],ze=0;
void min();
void main()
{
clrscr();
printf('Enter the no.of nodes:');
scanf('%d',&n);
printf('nEnter the source node:');
scanf('%d',&s);
printf('nEnter the no.of Neighbours to %d:',s);
scanf('%d',&nb);
printf('nEnter the Neighbours:');
for(i=1;i<=nb;i++)
scanf('%d',&nbs[i]);
printf('nEnter the timedelay form source to nbs:');
for(i=1;i<=nb;i++)
scanf('%d',&snbs[i]);
for(i=1;i<=nb;i++)
{
printf('nEnter the timedelay of %d: ',nbs[i]);
for(j=1;j<=n;j++)
scanf('%d',&delay[i][j]);
}
for(i=1;i<=nb;i++)
{
printf('nThe timedelays of %d: ',nbs[i]);
for(j=1;j<=n;j++)
printf('%3d',delay[i][j]);
}
min();
getch();
}
void min()
{
int sum,k,y=1,store=1;
printf('ntttnew- rout');
printf('nttttime-');
printf('ntttdelay');
printf('n');
for(i=1;i<=n;i++)
{
sum=0;
k=1;
for(j=1;j<=nb;j++)
{
temp[k++]=delay[j][i];
}
sum=temp[1]+snbs[1];
for(y=2;y<=nb;y++)
{
if(sum>temp[y]+snbs[y])
{
sum=temp[y]+snbs[y];
store=y;
}
}
if(si)
printf('nt%d+t%d =t%d --',ze,ze,ze);
else
printf('nt%d +t%d =t%dt%d',temp[store],snbs[store],sum,nbs[store]);
}
}
Output:
Aim:
Take an example subnet graph with weights indicating delay between nodes. Now obtain Routing table at each node using Distance Vector Routing.
Theory
Distance Vector routing (DVR) algorithm is unlike Dijkstra's algorithm which is a non-adaptive routing algorithm and means that it is purely static, that is pre-destined and fixed, not flexible in networks where congestions are more prone to occur. DVR is an adaptive routing algorithm in which the information from neighbours is maitained well by each and every node and this helps us to determine the simplest path possible in a changing network. Though, one of the node may fail, still, the destined node is reachable through other possible intermediate nodes that are found out by the DVR algorithm. The perfectly executing program below shows it live below.
Program:
#include
struct node
{
unsigned dist[20];
unsigned from[20];
}rt[10];
int main()
{
int dmat[20][20];
int n,i,j,k,count=0;
printf('nEnter the number of nodes : ');
scanf('%d',&n);
printf('nEnter the cost matrix :n');
for(i=0;i<>
for(j=0;j<>
{
scanf('%d',&dmat[i][j]);
dmat[i][i]=0;
rt[i].dist[j]=dmat[i][j];
rt[i].from[j]=j;
}
do
{
count=0;
for(i=0;i<>
for(j=0;j<>
for(k=0;k<>
if(rt[i].dist[j]>dmat[i][k]+rt[k].dist[j])
{
rt[i].dist[j]=rt[i].dist[k]+rt[k].dist[j];
rt[i].from[j]=k;
count++;
}
}while(count!=0);
for(i=0;i<>
{
printf('nnState value for router %d is n',i+1);
for(j=0;j<>
{
printf('tnnode %d via %d Distance%d',j+1,rt[i].from[j]+1,rt[i].dist[j]);
}
}
printf('nn');
}
Aim:
Take an example subnet of hosts. Obtain broadcast tree for it.
Theory
IP addressing is the allocation of unique ID to each and every system connected in a network to maintan communication among them through out the affixed network. There are 5 classes of IP Addresses namely A through E with the range varying from one class to the other class.
A subnet is a network allocation to similar systems or same hierarchial systems present in a allocated network like an organisation. Each and every system can be reachd through a client-server computing environment where the server acts as the Master and the clients acts as the Slaves to form a Master-Slave computing environment. Below programs show the calculation of network addresses with subnet predefinition and subnet generation.
Program:
a)Network Address:
#include
#include
void main()
{
unsigned int compad[4];
unsigned int mask[4];
unsigned int netadr[4];
int i;
clrscr();
printf('Enter the ip address:n');
scanf('%u%*c%u%*c%u%*c%u%*c',&compad[3],&compad[2],&compad[1],&compad[0]);
printf('Enter the subnet address:n');
scanf('%u%*c%u%*c%u%*c%u%*c',&mask[3],&mask[2],&mask[1],&mask[0]);
for(i=0;i<4;i++)
{
netadr[i]= compad[i]&mask[i];
}
printf('nNetwork address is:n');
printf('%u.%u.%u.%u',netadr[3],netadr[2],netadr[1],netadr[0]);
printf('nsubnet address is:n');
printf('%u.%u.%u.%u',mask[3],mask[2],mask[1],mask[0]);
printf('nip address is:n');
printf('%u.%u.%u.%u',compad[3],compad[2],compad[1],compad[0]);
getch();
}
Output:
b)Network address with automatic subnet address generation:
#include
#include
void main()
{
unsigned int compad[4];
unsigned int mask[4];
unsigned int netadr[4];
unsigned long int ma=0;
int i,pre;
clrscr();
printf('Enter the ip address:n');
scanf('%u%*c%u%*c%u%*c%u%*c',&compad[3],&compad[2],&compad[1],&compad[0]);
printf('Enter the prefix:n');
scanf('%ul',&pre);
for(i=(32-pre);i<32;i++)
ma=ma|(1<<>
for(i=0;i<4;i++)
{
mask[i]=ma%256;
ma=ma/256;
}
for(i=0;i<4;i++)
{
netadr[i]= compad[i]&mask[i];
}
printf('nNetwork address is:n');
printf('%u.%u.%u.%u',netadr[3],netadr[2],netadr[1],netadr[0]);
printf('nsubnet address is:n');
printf('%u.%u.%u.%u',mask[3],mask[2],mask[1],mask[0]);
printf('nip address is:n');
printf('%u.%u.%u.%u',compad[3],compad[2],compad[1],compad[0]);
getch();
}
Output:
Conclusion:
I personally found these programs very useful during my preparation for examinations. Not only from the examination point of view, I have used the above concepts in my academic as well as professional projects which also include concepts regarding Operating Systems, Compiler Design, Web Technologies and UML diagrams. A combination of all these concepts in terms of programs as depicted above would really mean a lot for every Computer Science backgroun student.

- Java RMI Tutorial
- Java RMI Useful Resources
- Selected Reading
RMI stands for Remote Method Invocation. It is a mechanism that allows an object residing in one system (JVM) to access/invoke an object running on another JVM.
RMI is used to build distributed applications; it provides remote communication between Java programs. It is provided in the package java.rmi.
Architecture of an RMI Application
In an RMI application, we write two programs, a server program (resides on the server) and a client program (resides on the client).
Inside the server program, a remote object is created and reference of that object is made available for the client (using the registry).
The client program requests the remote objects on the server and tries to invoke its methods.
The following diagram shows the architecture of an RMI application.
Let us now discuss the components of this architecture.
Transport Layer − This layer connects the client and the server. It manages the existing connection and also sets up new connections.
Stub − A stub is a representation (proxy) of the remote object at client. It resides in the client system; it acts as a gateway for the client program.
Skeleton − This is the object which resides on the server side. stub communicates with this skeleton to pass request to the remote object.
RRL(Remote Reference Layer) − It is the layer which manages the references made by the client to the remote object.
Working of an RMI Application
The following points summarize how an RMI application works −
When the client makes a call to the remote object, it is received by the stub which eventually passes this request to the RRL.
When the client-side RRL receives the request, it invokes a method called invoke() of the object remoteRef. It passes the request to the RRL on the server side.
The RRL on the server side passes the request to the Skeleton (proxy on the server) which finally invokes the required object on the server.
The result is passed all the way back to the client.
Marshalling and Unmarshalling
Whenever a client invokes a method that accepts parameters on a remote object, the parameters are bundled into a message before being sent over the network. These parameters may be of primitive type or objects. In case of primitive type, the parameters are put together and a header is attached to it. In case the parameters are objects, then they are serialized. This process is known as marshalling.
At the server side, the packed parameters are unbundled and then the required method is invoked. This process is known as unmarshalling.
RMI Registry
RMI registry is a namespace on which all server objects are placed. Each time the server creates an object, it registers this object with the RMIregistry (using bind() or reBind() methods). These are registered using a unique name known as bind name.
To invoke a remote object, the client needs a reference of that object. At that time, the client fetches the object from the registry using its bind name (using lookup() method).
The following illustration explains the entire process −
Goals of RMI
Download audio enhancement software torrent. Following are the goals of RMI −
- To minimize the complexity of the application.
- To preserve type safety.
- Distributed garbage collection.
- Minimize the difference between working with local and remote objects.
To write an RMI Java application, you would have to follow the steps given below −
- Define the remote interface
- Develop the implementation class (remote object)
- Develop the server program
- Develop the client program
- Compile the application
- Execute the application
Defining the Remote Interface
A remote interface provides the description of all the methods of a particular remote object. The client communicates with this remote interface.
To create a remote interface −
Create an interface that extends the predefined interface Remote which belongs to the package.
Declare all the business methods that can be invoked by the client in this interface.
Since there is a chance of network issues during remote calls, an exception named RemoteException may occur; throw it.
Following is an example of a remote interface. Here we have defined an interface with the name Hello and it has a method called printMsg().
Developing the Implementation Class (Remote Object)
We need to implement the remote interface created in the earlier step. (We can write an implementation class separately or we can directly make the server program implement this interface.)
To develop an implementation class −
- Implement the interface created in the previous step.
- Provide implementation to all the abstract methods of the remote interface.
Following is an implementation class. Here, we have created a class named ImplExample and implemented the interface Hello created in the previous step and provided body for this method which prints a message.
Developing the Server Program
An RMI server program should implement the remote interface or extend the implementation class. Here, we should create a remote object and bind it to the RMIregistry.
To develop a server program −
Create a client class from where you want invoke the remote object.
Create a remote object by instantiating the implementation class as shown below.
Export the remote object using the method exportObject() of the class named UnicastRemoteObject which belongs to the package java.rmi.server.
Get the RMI registry using the getRegistry() method of the LocateRegistry class which belongs to the package java.rmi.registry.
Bind the remote object created to the registry using the bind() method of the class named Registry. To this method, pass a string representing the bind name and the object exported, as parameters.
Following is an example of an RMI server program.
Developing the Client Program
Write a client program in it, fetch the remote object and invoke the required method using this object.
To develop a client program −
Create a client class from where your intended to invoke the remote object.
Get the RMI registry using the getRegistry() method of the LocateRegistry class which belongs to the package java.rmi.registry.
Fetch the object from the registry using the method lookup() of the class Registry which belongs to the package java.rmi.registry.
To this method, you need to pass a string value representing the bind name as a parameter. This will return you the remote object.
The lookup() returns an object of type remote, down cast it to the type Hello.
Finally invoke the required method using the obtained remote object.
Following is an example of an RMI client program.
Compiling the Application
To compile the application −
- Compile the Remote interface.
- Compile the implementation class.
- Compile the server program.
- Compile the client program.
Or,
Open the folder where you have stored all the programs and compile all the Java files as shown below.
Executing the Application
Step 1 − Start the rmi registry using the following command.
Program To Implement Crc In Java
This will start an rmi registry on a separate window as shown below.
Step 2 − Run the server class file as shown below.
Step 3 − Run the client class file as shown below.
Program To Implement Crc In Java Developer
Verification − As soon you start the client, you would see the following output in the server.
In the previous chapter, we created a sample RMI application. In this chapter, we will explain how to create an RMI application where a client invokes a method which displays a GUI window (JavaFX).
Defining the Remote Interface
Here, we are defining a remote interface named Hello with a method named animation() in it.
Developing the Implementation Class
In the Implementation class (Remote Object) of this application, we are trying to create a window which displays GUI content, using JavaFX. Dota 2 go launcher ex theme download.
Server Program
An RMI server program should implement the remote interface or extend the implementation class. Here, we should create a remote object and bind it to the RMIregistry.
Following is the server program of this application. Here, we will extend the above created class, create a remote object, and registered it to the RMI registry with the bind name hello.
Client Program
Following is the client program of this application. Here, we are fetching the remote object and invoking its method named animation().
Steps to Run the Example
Following are the steps to run our RMI Example.
Step 1 − Open the folder where you have stored all the programs and compile all the Java files as shown below.
Step 2 − Start the rmi registry using the following command.
This will start an rmi registry on a separate window as shown below.
Step 3 − Run the server class file as shown below.
Step 4 − Run the client class file as shown below.
Verification − As soon you start the client, you would see the following output in the server.
In the previous chapter, we created a sample RMI application where a client invokes a method which displays a GUI window (JavaFX).

In this chapter, we will take an example to see how a client program can retrieve the records of a table in MySQL database residing on the server.
Assume we have a table named student_data in the database details as shown below.
Assume the name of the user is myuser and its password is password.
Creating a Student Class

Create a Student class with setter and getter methods as shown below.
Defining the Remote Interface
Define the remote interface. Here, we are defining a remote interface named Hello with a method named getStudents () in it. This method returns a list which contains the object of the class Student.
Developing the Implementation Class
Create a class and implement the above created interface.
Program To Implement Crc In Java Runtime
Here we are implementing the getStudents() method of the Remote interface. When you invoke this method, it retrieves the records of a table named student_data. Sets these values to the Student class using its setter methods, adds it to a list object and returns that list.
Server Program
An RMI server program should implement the remote interface or extend the implementation class. Here, we should create a remote object and bind it to the RMI registry.
Following is the server program of this application. Here, we will extend the above created class, create a remote object and register it to the RMI registry with the bind name hello.
Client Program
Following is the client program of this application. Here, we are fetching the remote object and invoking the method named getStudents(). It retrieves the records of the table from the list object and displays them.
Steps to Run the Example
Following are the steps to run our RMI Example.
Step 1 − Open the folder where you have stored all the programs and compile all the Java files as shown below.
Step 2 − Start the rmi registry using the following command.
This will start an rmi registry on a separate window as shown below.
Program To Implement Crc In Java Compiler
Step 3 − Run the server class file as shown below.
Program To Implement Crc In Javascript
Step 4 − Run the client class file as shown below.
